Photo: Eric Feferberg/AFP/Getty Images
(Photo: Workers at their computers in an office in Paris. Ninety-three percent of cyber breaches are due to phishing and pretexting, with email being the most common entry point.)
 In the corporate world, the rise of cyber attacks is far outpacing the level of investment in protection from cyber threats: There has been a 33% increase in the cost of cybercrimes since 2016, but investments in cybersecurity lag behind, having only increased by 10%.
In the corporate world, the rise of cyber attacks is far outpacing the level of investment in protection from cyber threats: There has been a 33% increase in the cost of cybercrimes since 2016, but investments in cybersecurity lag behind, having only increased by 10%.
Digital adoption and technological innovation are allowing businesses to reach more people than ever before. But the further that digital nets are cast, the more opportunities cyber threat actors have to infiltrate company systems and data, while businesses and staff often don’t have the right combination of knowledge and tools to react to these threats.
A recent report by Marsh & McLennan Insights and FireEye, an intelligence-led security company, addresses the need for organizations to prioritize cyber resilience over traditional cyber defense approaches.
Most security breaches come from email
 The most vulnerable part of a company’s cybersecurity is its employees. Cyber threat actors rely on them to click links or open files that release malware into the system. Threat actors also assume false identities in conversation with company employees to collect sensitive data in the process.
The most vulnerable part of a company’s cybersecurity is its employees. Cyber threat actors rely on them to click links or open files that release malware into the system. Threat actors also assume false identities in conversation with company employees to collect sensitive data in the process.
Ninety-three percent of cyber breaches are due to phishing and pretexting, with email being the most common entry point at 96%.
According to the report, “more than 90% of cyber incidents are caused by social engineering techniques,” which rely on “human interaction to gain trust and manipulate[s] people into breaking standard security practices.”
Protection from these incidents can start with everyone at the company, regardless of department. If all staff are educated on how to identify phishing emails and verify supposed company partners, they could be the most effective defense against cyber breaches. However, a report on evidence-based malware cybersecurity training for employees shows that awareness of cyber risks isn’t enough to change employee behavior. The report states that the motivating factor for employees to take preventive action is an awareness of their own personal risk that goes along with being involved in a cybersecurity breach or attack.
The other imperative element of a cyber risk strategy, especially in terms of resiliency, is cyber risk insurance.
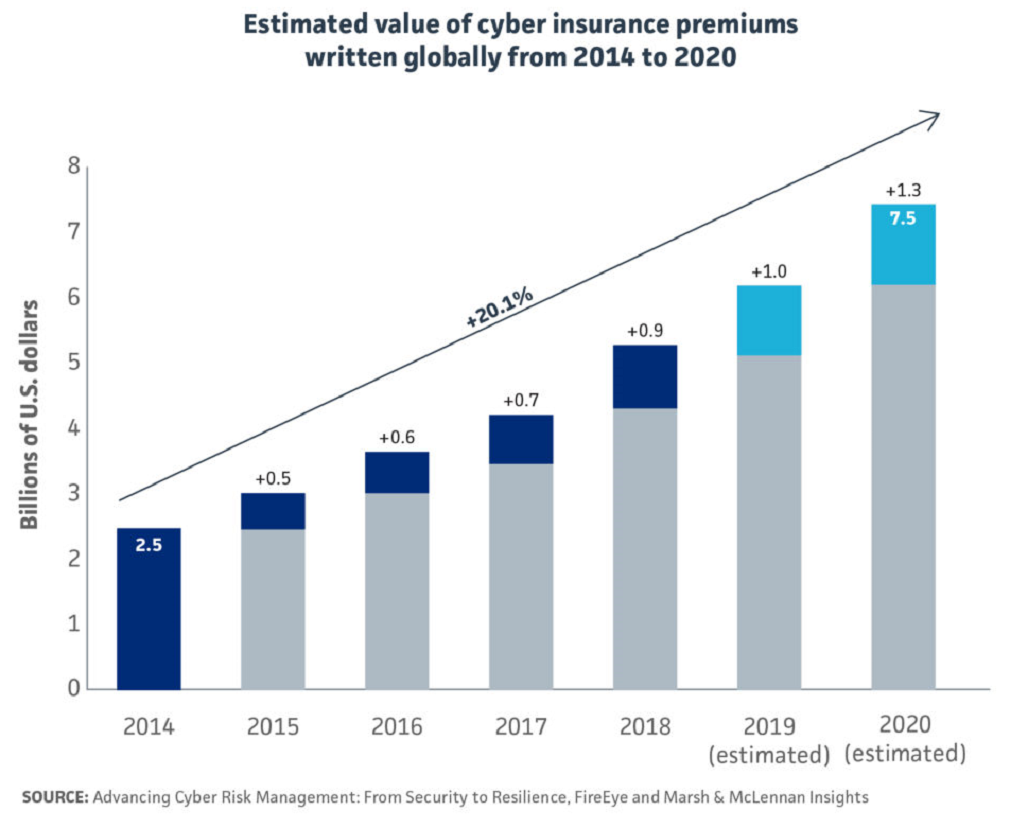
Cyber insurance outpacing all other insurance
Due to an expanding market for cyber insurance, premiums are growing “three times faster than the general property-casualty insurance market,” according to the report. They are expected to increase at “a compounded annual growth rate of 20.1%, between 2014 and 2020.”
The high cost of cyber insurance premiums is due in part to having a high risk exposure, but insurers’ lack of visibility into company risk profiles also drives up the cost of premiums. Thus, in addition to safeguarding your systems and data, a cybersecurity and resilience strategy — made transparent to the insurer — may lower cyber insurance premiums.
Cyber risk insurance can hasten the rebound from risk events involving anything from data restoration, data breach fines and payment to PR firms for handling post-breach communications. Some insurers will even cover social engineering fraud.
Insurance cost is also affected by policy. The World Economic Forum’s report on cyber resilience notes that cyber insurance can be voluntary, incentivized or mandated, with financial trade offs for each option. With voluntary insurance, the upfront cost for insurers are lower due to a lack of security controls, but over time, the cost would be too great to maintain; with mandated insurance, companies would pay more up front for a more sustainable cost structure in the long term, accompanied by security controls on the cost of insurance.
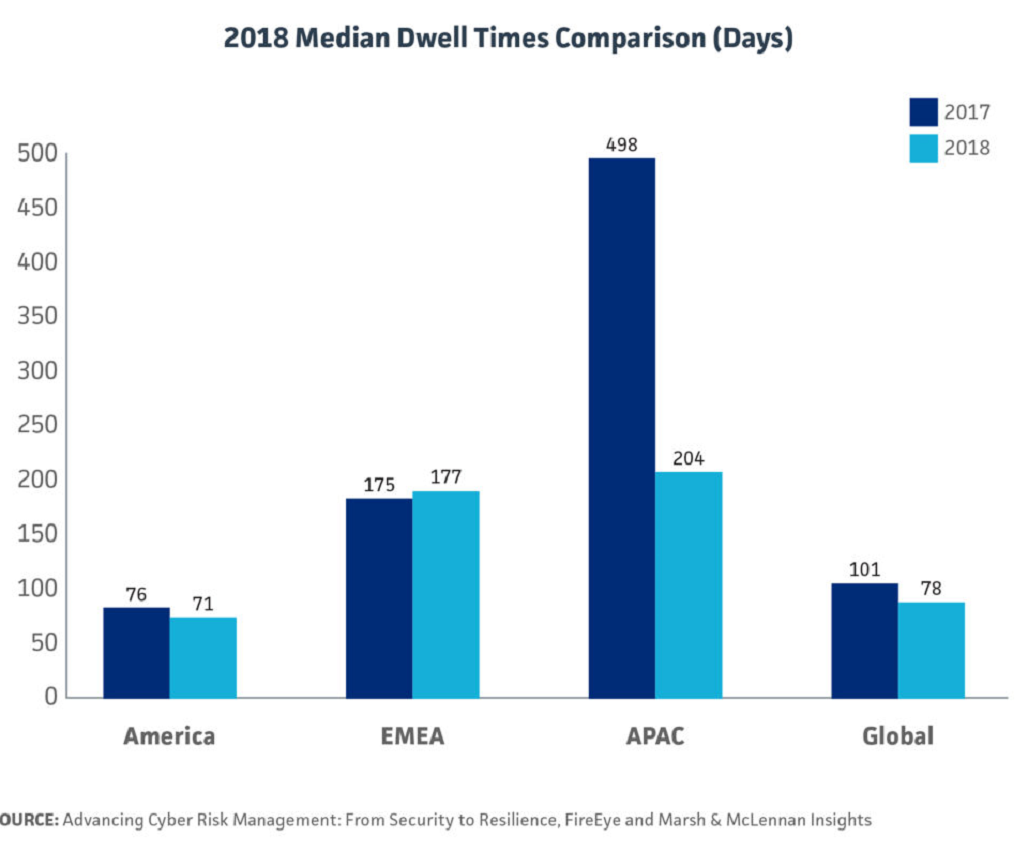
A drop in dwell times
Despite the global lag in investing in cybersecurity, there are some encouraging trends, especially in dwell time, which is “the number of days an attacker is present on a victim network, from first evidence of compromise to detection.”
In 2018, dwell time decreased by 23 days to 78 globally compared to 2017. Asia-Pacific still has the highest dwell time at 204 days, but since 2017, its dwell time has plummeted to 204 from 498, decreasing by 294 days in one year.
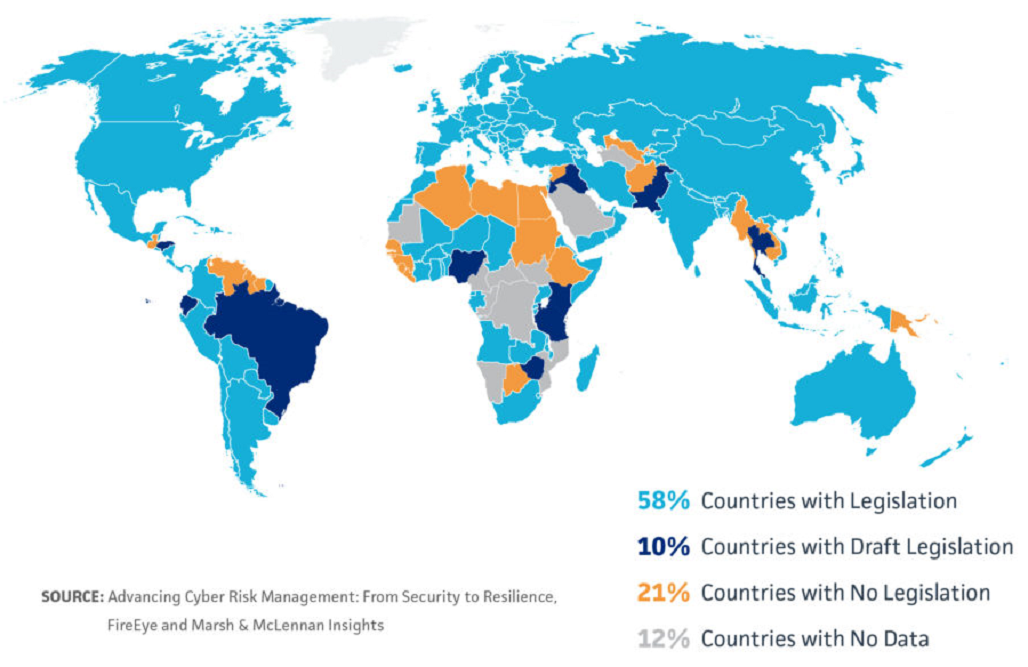
There are other positive trends in data security policy being implemented across the globe, especially following the implementation of GDPR. Sixty-eight percent of countries have either implemented data protection policies or have drafted legislation to do so.
Closing the gap
The mission in cybersecurity is not necessarily to wholly avoid breaches and attacks, but to know how to respond intelligently and systematically when they happen — because it’s likely they will.
According to the report, there are three steps to strengthening cyber resilience: 1) understanding business vulnerabilities, 2) understanding the level of risk that can be absorbed and 3) understanding tools and strategies for cyber threat protection. Focusing time and investments on strategic reactions to cyber breaches and attacks and considering a company’s entire staff as the first line of defense can strengthen cybersecurity considerably. With this approach, the global level of investment in cybersecurity may begin to increase at least at the same rate as the climbing costs of cybercrime.
Related themes: Cybersecurity Regulation
The original Brink’s article can be read HERE.

Leave a Reply