Promoting Cooperation in Cyber Security Management
Introduction
 (1) Cyber threats have become ubiquitous and unseen. They can come from various actors including criminals, hacktivists, competitors, or disgruntled employees and the outcomes include disruption of infrastructure, large-scale theft of personal data and hacking of financial and payment system, which cause significant losses. Cyber-attacks are becoming more advanced and sophisticated. Some attacks are indiscernible until they actually occur. To tackle with this inevitable trend requires not only robust cyber security defence by a single entity, but also crossvector cooperation among banks, law enforcement agencies, regulators and the public.
(1) Cyber threats have become ubiquitous and unseen. They can come from various actors including criminals, hacktivists, competitors, or disgruntled employees and the outcomes include disruption of infrastructure, large-scale theft of personal data and hacking of financial and payment system, which cause significant losses. Cyber-attacks are becoming more advanced and sophisticated. Some attacks are indiscernible until they actually occur. To tackle with this inevitable trend requires not only robust cyber security defence by a single entity, but also crossvector cooperation among banks, law enforcement agencies, regulators and the public.
(2) This position paper discusses a structured Cyber Security Cooperation model (see Figure 1), based on the People, Process, Technology Framework, for strengthening the cyber security controls to prevent cyber-attacks and to minimize the impact of successful attacks.
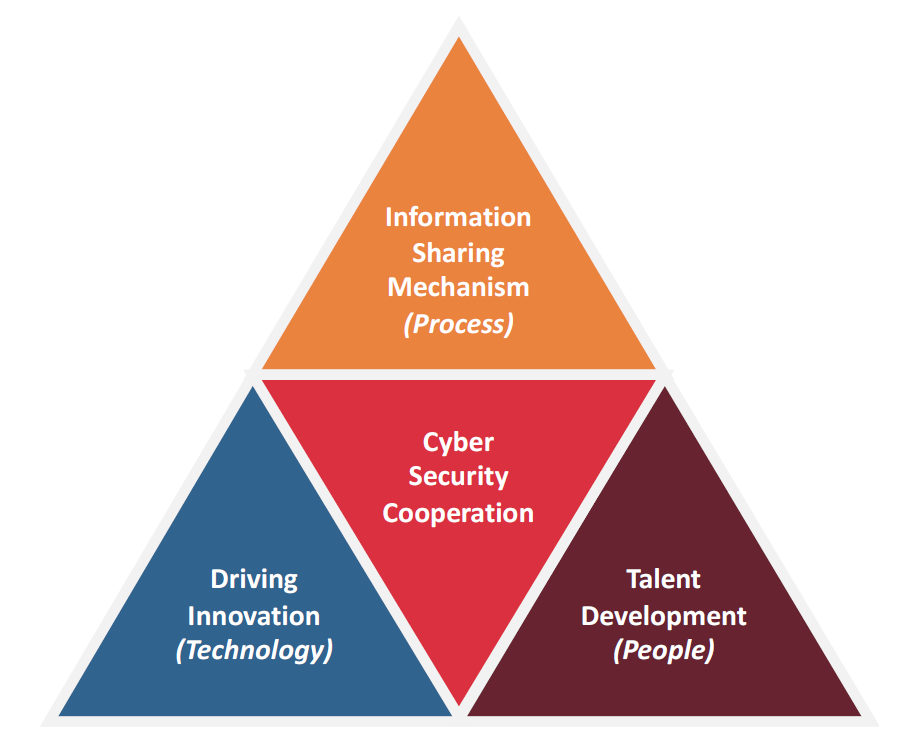
Figure 1 – Three Key Pillars of Cyber Security Cooperation
Cyber Security Cooperations
(3) Cyberspace becomes one of the key influencers and drivers of the social and economic growth by providing new means for people connection, interaction and collaboration. In parallel, the cyberspace is a fast-growing area of crime, where criminals can remain anonymous while preying on victims. Everyone can be a victim and cyber security therefore becomes everyone’s responsibility.
(4) Cyberspace expands rapidly, where cyber incidents and risks are inevitable. It will be ideal if one expects complete prevention of cyber-attacks merely by implementing controls. Instead, a principle-based approach of cyber resilience should be adopted with a focus to prevent further damage through a proactive and timely cooperation with peers and authorities. Such cooperation can be established in the form of committees and task forces driven by industry peers, bureau or regulators. This can help articulate the cyber threats and develop the institutionalised mechanism in protecting the cyberspace.
(5) Take Hong Kong as an example: Being one of the leading international financial centres and as a prime location for financial technology (“Fintech”) development, Hong Kong continues to strengthen and promote cyber security cooperation at various level:
(5.1) Introducing the Cybersecurity Fortification Initiative (“CFI”) to the banking industry – In collaboration with the banking industry, the Hong Kong Monetary Authority (“HKMA”) has introduced a three-pillar programme on cyber resilience framework, professional development and intelligence sharing since 2016i. The HKMA has also revampedii its cyber resilience framework in response to new security areas including cloud technology and virtualization, etc.
(5.2) Uplifting the cyber security services to critical infrastructure – In addition to the upgrade of Cyber Security and Technology Crime Bureau (“CSTCB”) by the Hong Kong Police Force (“HKPF”) in 2015iii, HKPF is committed to enhance the cyber security of critical infrastructure in Hong Kong since 2016 through proactive cyber security monitoring iv , cyber security drill v , communication channels on cyber security trend and dedicated security trainings for the industry practitionersvi.
(5.3) Establishing dedicated taskforces and working groups for various industries – Besides the Hong Kong Computer Emergency Response Team Coordination Centre (“HKCERT”) vii , multiple task forces and working groups have been established with active participation by industry leaders for each industry, especially for the banking industry, to streamline cyber-attack analysis and expand the cyber security defense frontier.
(6) A strong culture of cyber security cooperation raises a synergy effect in defensing cyber-attacks and combating cyber-crimes. Meanwhile, an effective cyber security information sharing mechanism is indispensable.
Cyber Security Information Sharing
(7) Overwhelming cyber threats, vulnerabilities and innovative cyber-attacks challenge the cyber resilience capabilities of an organisation, where no single organisation has the knowledge covering all of these. Cyber security information sharing becomes a critical and effective tool for the cyber security function of an organisation to avoid the faults other industry peers come across.
(8) Successful information sharing should not be limited to Indicators of Compromise (“IOCs”) sharing only, it also requires contributions in various aspects, such as sharing of cyber-attacks approach and guidance on defense measures at different layers to support better decision-making in cyber security management.
(9) While an effective cyber security information sharing requires a centralized mechanism for effective and timely sharing the information, a centralised and community-driven platform is one of the most effective mechanisms. For example, back to 2017, the law enforcement agencies, the HKMA and the cyber security communities of Hong Kong established a cyber threat intelligence platform for the banking industryviii and eventually launched the platform across all industries in 2018ix.
(10) Another effective means of cyber security information sharing is the cyber security advisory mechanism driven by the law enforcement and regulators. Law enforcement and regulators, as a centralised information hub, can alert the communities on the threat intelligence, e.g. details about recent cyber-attacks collected from the victims.
(11) Proactive information sharing on cyber-attacks and cyber-defense is one of the critical success factors in building effective cyber resilience and evolving immunity across industries and regions. With the support of these information, emerging cyber security innovation can drive and realise the effective resilience solutions.
Driving Innovation
(12) Innovation and digital transformation play a major role in modern banking. While customer experiences are continuously enhanced with increasingly seamless and integrated services, the cybersecurity risks induced cannot be overlooked. Traditional use of technologies, information security approach and processes may not able to fully address and respond to the incidents and risks triggered by cybercrime.
(13) In recent years, the banking industry is undergoing transformation. New business initiatives such as OpenAPI and remote account opening, etc. are evolving. To cope with the risks of these banking innovations, banks’ control functions should work hand-in-hand with the business in understanding the underlying technology solutions and evaluating relevant security risks and controls. Guideline and baseline requirements should be formulated to facilitate a standardised and riskcontrolled technology adoption journey while enable the bank to quickly address customers’ need in a highly competitive market.
(14) The regulators also have a role to play; they should display prompt supervisory efforts to guide the industry in managing the relevant emerging risks induced by innovations. Good examples include circulars and guidelines issued by the HKMA on remote account openingx and artificial intelligencexi to remind the industry of the risk in adopting relevant technologies as well as to share sound practices observed in the industry. “Regtech Watch”xii is also published regularly to socialise cutting-edge uses cases in risk management and regulatory compliance. It is expected to see regulators taking a proactive approach in its supervision to drive industry innovation going forward.
(15) In addition, to further foster a culture of innovation, regulatory sandbox approach can empower banks to pilot run their initiatives, together with their partnering technology firms, in a controlled environment (e.g. only to internal staff and limited number of customers) without full compliance to the regulatory requirements. It allows banks to understand the readiness of their services and relevant cyber security controls and potential weaknesses prior to public launch.
Talent Development
(16) To sustain both sharing and innovation, “People” is the most important element in bringing a successful cyber security cooperation.
(17) According to a recent study carried out by the Information Systems Audit and Control Association (“ISACA”), an international professional body focusing on IT governance and information security, there is a significant gap in cyber security talents especially highly skilled cybersecurity workforce.
“The cybersecurity skills gap has been plaguing enterprises for years – but despite garnering much discussion and media coverage, little progress is being made.” xiii
(18) In the face of such challenge, a multiparty-driven and industry-wide programme should be implemented to uplift the competency standards and enable effective trainings for enhancing the capabilities of cyber security practitioners. Take Hong Kong as an example again:
(18.a) Uplifting the competency standards – While banks are looking for talents with appropriate cyber security skills, the HKMA had implemented the Enhanced Competency Framework on Cybersecurity (“ECF-C”) xiv in collaboration with the banking industry. The framework was designed and benchmarked against the Council of Registered Ethnical Security Testers (“CREST”), an international cybersecurity standard initiated by the CREST organisation in the United Kingdomxv.
(18.b) Enabling effective trainings – A Cyber Range facility has been established by the Hong Kong Applied Science and Technology Research Institute (“ASTRI”) in collaboration with the HKPF to provide cybersecurity training services to professionals from law enforcement agencies as well as the financial services industry since 2016xvi.
Conclusion
(19) While individuals, banks, law enforcement agencies and regulators are continuously seeking innovative ways in using cyberspace to their advantage, many of them, at the same time, have been/will be victims of the cyber-attacks and cyber-crimes. The damage posed are significant and some of them may not even be able to recover.
(20) The ultimate goal of a structured cyber security cooperation is not to completely prevent cyber-attacks. Instead, the structured model discussed in this paper aims to excel the cyber resilience capabilities of a single entity by leveraging the knowledge and experiences across industries and regions.
(21) The Next Step: While cyber-attacks would never be stopped as long as the cyberspace exists, it is necessary to continuously advance and deepen the cyber security cooperation and putting this as one of the highest priority items in the cyber security strategy.
The presentation file can be downloaded HERE.
Prepared for the Asian Bankers Association by:
 Eric Wong
Eric Wong
Group Chief Information Officer
General Manager and Head of Technology and Productivity Division
The Bank of East Asia, Limited
References:
i Circular on Cybersecurity Fortification Initiative, Hong Kong Monetary Authority, 24 May 2016
https://www.hkma.gov.hk/media/eng/doc/key-information/guidelines-and-circular/2016/20160524e1.pdf
ii Circular on Cybersecurity Fortification Initiative 2.0, Hong Kong Monetary Authority, 3 Nov 2020
https://www.hkma.gov.hk/media/eng/doc/key-information/guidelines-and-circular/2020/20201103e1.pdf
iii LCQ22: Enhancing Cyber Security and Combating Technology Crimes, The Government of the HKSAR, 22
Nov 2017 https://www.info.gov.hk/gia/general/201711/22/P2017112200672.htm
iv LCQ19: Information Security in Hong Kong, The Government of the HKSAR, 14 Dec 2016
https://www.info.gov.hk/gia/general/201612/14/P2016121400637.htm
v Issues Relating to Protection of Personal Data and Cyber Security, Legislative Council, 14 Nov 2018
https://www.legco.gov.hk/yr18-19/english/panels/itb/papers/caitbse20181114cb2-222-3-e.pdf
vi Press Release – CSTCB hosts Online Service Providers Symposium, The Hong Kong Police Force, 17 Apr 2018
https://www.police.gov.hk/offbeat/1108/eng/6502.html
vii Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT)
https://www.hkcert.org
viii Regulatory Keynote Speech – Balancing Innovation and Risk, Hong Kong Monetary Authority, 22 Mar 2019
https://www.hkma.gov.hk/media/eng/doc/key-information/speeches/s20190322e1.pdf
ix Update on Information Security, Legislative Council, 13 Jan 2020
https://www.legco.gov.hk/yr19-20/english/panels/itb/papers/itb20200113cb1-306-5-e.pdf
x Circular on Coronavirus disease (COVID-19) and Anti-Money Laundering and Counter- Financing of
Terrorism (AML/CFT) measures, Hong Kong Monetary Authority, 7 Apr 2020
https://www.hkma.gov.hk/media/eng/doc/key-information/guidelines-and-circular/2020/20200407e1.pdf
xi Report on “Artificial Intelligence in Banking: The Changing Landscape in Compliance and Supervision”,
Hong Kong Monetary Authority, 21 Aug 2020
https://www.hkma.gov.hk/eng/news-and-media/press-releases/2020/08/20200821-3/
xii Regtech Watch Issue No. 1, Hong Kong Monetary Authority, Nov 2019
https://www.hkma.gov.hk/media/eng/doc/key-information/guidelines-and-rcular/2019/20191112e1a1.pdf
xiii State of Cybersecurity 2020 – Part 1: Global Update on Workforce Efforts and Resources, Information
Systems Audit and Controls Association, https://www.isaca.org/go/state-of-cybersecurity-2020
xiv Circular on Enhanced Competency Framework on Cybersecurity, Hong Kong Monetary Authority, 19 Dec
2016 https://www.hkma.gov.hk/media/eng/doc/key-information/guidelines-andcircular/
2016/20161219e1.pdf
xv Cybersecurity Advancement Programme for Banking Industry in Hong Kong, The Hong Kon Institute of
Bankers, 15 Apr 2019 http://www.hkib.org/storage/files/65/HKIB_report20190601.pdf
xvi Cyber Range Overview, Hong Kong Applied Science and Technology Research Institute
https://www.astri.org/technologies/joint-research-laboratories/rd-centres/cyber-range